釣魚 (網絡)
閱讀設定
(由網絡釣魚跳轉過嚟)

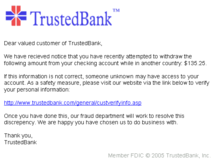
(收到呢封 e-mail 嘅人一撳條拎就出事。)
電腦保安上講嘅
概論
[編輯]睇埋:電腦保安
一場釣魚式嘅攻擊過程如下[1]:
- 攻擊方假扮成一啲信得過嘅人或者組織,例如扮成銀行或者政府嘅人員呀噉;
- 向受害方傳信息或者電郵,而且提到一啲會令受害方「揗雞,想即刻行動」嘅內容,例如「我哋係 XX 銀行,你個戶口喺三日前畀一個身處美國嘅人提咗咁多咁多錢」噉;
- 靠呢種信息或者電郵引受害方提供一啲敏感資訊,例如「如果啲錢唔係你提取嘅,麻煩撳下面條拎,提供你嘅信用咭號碼」噉;
- 釣魚式攻擊通常會配合埋各種嘅惡意軟件嚟用,受害方一撳條拎,就會出事-可能條拎會連去一個叫受害方填敏感資訊嘅網站,甚至一撳條拎隻惡意軟件就會單撈落受害方部機度。
黑客寫好信息設好條拎之後,就向 1,000 個人 send(粵拼:sen1)釣魚電郵,梗會有一兩個人上當[2]。
進階啲嘅釣魚式攻擊仲可以好個人化(魚叉式釣魚)-例如黑客望到某個人手上有啲價值連城嘅資產,就走去調查吓嗰個人,知佢有咩朋友,跟住喺釣魚用嘅電郵度模仿佢啲朋友嘅口吻寫嘢。
應對
[編輯]事實表明,釣魚式攻擊可以造成巨大嘅損失,例如喺 2020 年代初就出咗好多單,有黑客用釣魚式攻擊引人撳拎,用拎嘅惡意軟件嚟偷走值成幾廿萬美金嘅 NFT [3],甚至仲有荷里活嘅演員畀人透過呢種方法偷走佢嘅 NFT 資產[4]。因為噉,有唔少電腦保安工作者都有研究點樣對付釣魚式攻擊,例如反垃圾電郵技術就可以用嚟減少啲人睇到釣魚用電郵嘅機率。
下面段文未譯好,歡迎你幫手。
睇埋
[編輯]攷
[編輯]
- ↑ [1]
- ↑ Phishing Scams: Hook, Line, and Sinker. Stevenson University Online.
- ↑ Bored Ape NFTs Worth $135K Stolen by Prolific Phishing Thief. BeInCrypto.
- ↑ 4 NFTs Including a Bored Ape Stolen From Hollywood Actor Seth Green. Crypto Potato.
- ↑ Jakobsson, Markus. "The Human Factor of Phishing" (PDF). Privacy & Security of Consumer Information '07. 原著 (PDF)喺2007年9月13號歸檔. 喺February 2搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Tan, Koon. "Phishing and Spamming via IM (SPIM)". Internet Storm Center. 喺Dec 5搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Skoudis, Ed (June 13, 2006). "Phone phishing: The role of VoIP in phishing attacks". searchSecurity.
- ↑ ""phish, v." OED Online, March 2006, Oxford University Press". Oxford English Dictionary Online. 喺Aug 9搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Ollmann, Gunter. "The Phishing Guide: Understanding and Preventing Phishing Attacks". Technical Info. 喺Jul 10搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Felix, Jerry and Hauck, Chris (September 1987). "System Security: A Hacker's Perspective". 1987 Interex Proceedings. 1: 6.
{{cite journal}}: CS1 maint: multiple names: 作者名單 (link)
- ↑ "Spam Slayer: Do You Speak Spam?". PCWorld.com. 原著喺2007年9月30號歸檔. 喺Aug 16搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ ""phishing, n." OED Online, March 2006, Oxford University Press". Oxford English Dictionary Online. 喺Aug 9搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Phishing". Language Log, September 22, 2004. 喺Aug 9搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Mitchell, Anthony (July 12, 2005). "A Leet Primer". TechNewsWorld. 原著喺2007年12月9號歸檔. 喺2007年8月13號搵到.
{{cite news}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ "Know your Enemy: Phishing". The Honeynet Project & Research Alliance. 原著喺2018年3月20號歸檔. 喺Jul 8搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Phishing". Word Spy. 原著喺2014年10月15號歸檔. 喺Sep 28搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Stutz, Michael (January 29, 1998). "AOL: A Cracker's Paradise?". Wired News. 原著喺2005年12月22號歸檔. 喺2007年8月13號搵到.
- ↑ "History of AOL Warez". 原著喺2011年1月31號歸檔. 喺Sep 28搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "GP4.3 - Growth and Fraud - Case #3 - Phishing". Financial Cryptography. Dec 30, 2005.
- ↑ "In 2005, Organized Crime Will Back Phishers". IT Management. Dec 23, 2004.
- ↑ "The economy of phishing: A survey of the operations of the phishing market". First Monday. Sep 2005. 原著喺2012年11月24號歸檔. 喺2007年8月13號搵到.
{{cite web}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ "Suspicious e-Mails and Identity Theft". Internal Revenue Service. 原著喺2011年1月31號歸檔. 喺Jul 5搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Phishing for Clues". Indiana University Bloomington. September 15, 2005.
- ↑ "What is spear phishing?". Microsoft Security At Home. 喺Jul 10搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Kirk, Jeremy (June 02, 2006). "Phishing Scam Takes Aim at MySpace.com". IDG Network. 原著喺2006年6月16號歸檔. 喺2007年8月13號搵到.
{{cite news}}: Check date values in: |date= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ "Malicious Website / Malicious Code: MySpace XSS QuickTime Worm". Websense Security Labs. 喺Dec 5搵到.
{{cite web}}: Check date values in: |accessdate= (help); Cite has empty unknown parameter: |1= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Tom Jagatic and Nathan Johnson and Markus Jakobsson and Filippo Menczer. "Social Phishing" (PDF). To appear in the CACM (Oct 2007). 喺Jun 3搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Berners-Lee, Tim. "Uniform Resource Locators (URL)". IETF Network Working Group. 喺January 28搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Microsoft. "A security update is available that modifies the default behavior of Internet Explorer for handling user information in HTTP and in HTTPS URLs". Microsoft Knowledgebase. 喺August 28搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Fisher, Darin. "Warn when HTTP URL auth information isn't necessary or when it's provided". Bugzilla. 喺August 28搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Johanson, Eric. "The State of Homograph Attacks Rev1.1". The Shmoo Group. 原著喺2005年8月23號歸檔. 喺August 11搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Evgeniy Gabrilovich and Alex Gontmakher (February 2002). "The Homograph Attack" (PDF). Communications of the ACM. 45(2): 128. 原著 (PDF)喺2006年1月30號歸檔. 喺2007年8月13號搵到.
{{cite journal}}: More than one of |accessdate=、|access-date= specified (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ Leyden, John (August 15, 2006). "Barclays scripting SNAFU exploited by phishers". The Register.
- ↑ Levine, Jason. "Goin' phishing with eBay". Q Daily News. 喺December 14搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Mutton, Paul. "Phishing Web Site Methods". FraudWatch International. 原著喺2011年1月31號歸檔. 喺December 14搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Phishing con hijacks browser bar". BBC News. April 8, 2004.
- ↑ Krebs, Brian. "Flaws in Financial Sites Aid Scammers". Security Fix. 喺June 28搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Mutton, Paul. "PayPal Security Flaw allows Identity Theft". Netcraft. 喺June 19搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Hoffman, Patrick (January 10, 2007). "RSA Catches Financial Phishing Kit". eWeek. 原著喺2019年7月1號歸檔. 喺2007年8月13號搵到.
{{cite news}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ Gonsalves, Antone (April 25, 2006). "Phishers Snare Victims With VoIP". Techweb. 原著喺2007年3月28號歸檔. 喺2007年8月13號搵到.
{{cite news}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ "Identity thieves take advantage of VoIP". Silicon.com. March 21, 2005. 原著喺2005年3月24號歸檔. 喺2007年8月13號搵到.
{{cite news}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ Mutton, Paul. "Fraudsters seek to make phishing sites undetectable by content filters". Netcraft. 喺Jul 10搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Virgil Griffith and Markus Jakobsson. "Messin' with Texas, Deriving Mother's Maiden Names Using Public Records" (PDF). ACNS '05. 原著 (PDF)喺2006年7月5號歸檔. 喺Jul 7搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Krebs, Brian (November 18, 2004). "Phishing Schemes Scar Victims". washingtonpost.com.
- ↑ Kerstein, Paul (July 19, 2005). "How Can We Stop Phishing and Pharming Scams?". CSO. 原著喺2006年2月20號歸檔. 喺2007年8月13號搵到.
{{cite news}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ "UK phishing fraud losses double". Finextra. March 07, 2006. 原著喺2009年1月19號歸檔. 喺2007年8月13號搵到.
{{cite news}}: Check date values in: |date= (help)
- ↑ Richardson, Tim (May 3, 2005). "Brits fall prey to phishing". The Register.
- ↑ Miller, Rich. "Bank, Customers Spar Over Phishing Losses". Netcraft. 喺Dec 14搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ 〈存档副本〉。原著喺2008年10月7號歸檔。喺2007年8月13號搵到。
{{cite web}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ 〈存档副本〉。原著喺2008年10月28號歸檔。喺2007年8月13號搵到。
{{cite web}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ Ponnurangam Kumaraguru, Yong Woo Rhee, Alessandro Acquisti, Lorrie Cranor, Jason Hong and Elizabeth Nunge. (November 2006.). "Protecting People from Phishing: The Design and Evaluation of an Embedded Training Email System" (PDF). Technical Report CMU-CyLab-06-017, CyLab, Carnegie Mellon University. 原著 (PDF)喺2007年1月30號歸檔. 喺Nov 14搵到.
{{cite web}}: Check date values in: |accessdate=、|date= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)CS1 maint: multiple names: 作者名單 (link)
- ↑ Bank, David (August 17, 2005). "'Spear Phishing' Tests Educate People About Online Scams". The Wall Street Journal. 原著喺2011年4月6號歸檔. 喺2007年8月13號搵到.
- ↑ "Anti-Phishing Tips You Should Not Follow". HexView. 原著喺2008年3月20號歸檔. 喺June 19搵到.
{{cite web}}: Check date values in: |accessdate= (help); Cite has empty unknown parameter: |1= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Protect Yourself from Fraudulent Emails". PayPal. 原著喺2011年4月6號歸檔. 喺July 07搵到.
{{cite web}}: Check date values in: |accessdate= (help); Cite has empty unknown parameter: |1= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Markus Jakobsson, Alex Tsow, Ankur Shah, Eli Blevis, Youn-kyung Lim. "What Instills Trust? A Qualitative Study of Phishing" (PDF). USEC '06. 原著 (PDF)喺2007年3月6號歸檔. 喺2007年8月13號搵到.
{{cite web}}: Cite has empty unknown parameter: |1= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)CS1 maint: multiple names: 作者名單 (link)
- ↑ Zeltser, Lenny (March 17, 2006). "Phishing Messages May Include Highly-Personalized Information". The SANS Institute. 原著喺2006年12月2號歸檔. 喺2007年8月13號搵到.
- ↑ Markus Jakobsson and Jacob Ratkiewicz. "Designing Ethical Phishing Experiments" (PDF). WWW '06. 原著 (PDF)喺2006年7月24號歸檔. 喺2007年8月13號搵到.
{{cite web}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ Kawamoto, Dawn (August 4, 2005). "Faced with a rise in so-called pharming and crimeware attacks, the Anti-Phishing Working Group will expand its charter to include these emerging threats". ZDNet India. 原著喺2006年1月14號歸檔. 喺2007年8月13號搵到.
- ↑ Brandt, Andrew. "Privacy Watch: Protect Yourself With an Antiphishing Toolbar". PC World - Privacy Watch. 原著喺2011年6月5號歸檔. 喺Sep 25搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Franco, Rob. "Better Website Identification and Extended Validation Certificates in IE7 and Other Browsers". IEBlog. 喺May 20搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Bon Echo Anti-Phishing". Mozilla. 喺June 02搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Gone Phishing: Evaluating Anti-Phishing Tools for Windows". 3Sharp. September 27, 2006. 原著喺2008年1月14號歸檔. 喺October 20搵到.
{{cite news}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Two Things That Bother Me About Google's New Firefox Extension". Nitesh Dhanjani on O'Reilly ONLamp. 喺July 01搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Firefox 2 Phishing Protection Effectiveness Testing". 喺January 23搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Higgins, Kelly Jackson. "DNS Gets Anti-Phishing Hook". Dark Reading. 原著喺2011年8月18號歸檔. 喺October 8搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Krebs, Brian (August 31, 2006). "Using Images to Fight Phishing". Security Fix.
- ↑ Seltzer, Larry (August 2, 2004). "Spotting Phish and Phighting Back". eWeek.
- ↑ Bank of America. "How Bank of America SiteKey Works For Online Banking Security". 喺January 23搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Brubaker, Bill (July 14, 2005). "Bank of America Personalizes Cyber-Security". Washington Post.
- ↑
Stone, Brad (February 5, 2007). "Study Finds Web Antifraud Measure Ineffective". New York Times. 喺February 5搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Stuart Schechter, Rachna Dhamija, Andy Ozment, Ian Fischer (May, 2007). "The Emperor's New Security Indicators: An evaluation of website authentication and the effect of role playing on usability studies" (PDF). IEEE Symposium on Security and Privacy, May 2007. 原著 (PDF)喺2008年7月20號歸檔. 喺February 5搵到.
{{cite web}}: Check date values in: |accessdate=、|date= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)CS1 maint: multiple names: 作者名單 (link)
- ↑ "Phishers target Nordea's one-time password system". Finextra. October 12, 2005. 原著喺2005年12月18號歸檔. 喺2007年8月13號搵到.
- ↑ Krebs, Brian (July 10, 2006). "Citibank Phish Spoofs 2-Factor Authentication". Security Fix.
- ↑
Schneier, Bruce. "Security Skins". Schneier on Security. 喺December 3搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Rachna Dhamija, J.D. Tygar (July, 2005). "The Battle Against Phishing: Dynamic Security Skins" (PDF). Symposium On Usable Privacy and Security (SOUPS) 2005. 原著 (PDF)喺2007年6月29號歸檔. 喺February 5搵到.
{{cite web}}: Check date values in: |accessdate=、|date= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Ian Fette, Norman Sadeh, Anthony Tomasic (June 2006). "Learning to Detect Phishing Emails" (PDF). Carnegie Mellon University Technical Report CMU-ISRI-06-112.
{{cite web}}: CS1 maint: multiple names: 作者名單 (link)
- ↑ "Anti-Phishing Working Group: Vendor Solutions". Anti-Phishing Working Group. 原著喺2012年10月5號歸檔. 喺July 06搵到.
{{cite web}}: Check date values in: |accessdate= (help); Cite has empty unknown parameter: |1= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ McMillan, Robert (March 28, 2006). "New sites let users find and report phishing". LinuxWorld. 原著喺2009年1月19號歸檔. 喺2007年8月13號搵到.
{{cite news}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ "PhishTank - A New Collaborative Phishing Workgroup". limited-exposure. 喺Oct 03搵到.
{{cite web}}: Check date values in: |accessdate= (help); Cite has empty unknown parameter: |1= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)CS1 maint: url-status (link)
- ↑ Legon, Jeordan (January 26, 2004). "'Phishing' scams reel in your identity". CNN.
- ↑ Leyden, John (March 21, 2005). "Brazilian cops net 'phishing kingpin'". The Register.
- ↑ Roberts, Paul (June 27, 2005). "UK Phishers Caught, Packed Away". eWEEK. 原著喺2019年7月1號歸檔. 喺2007年8月13號搵到.
{{cite news}}: More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ "Nineteen Individuals Indicted in Internet 'Carding' Conspiracy". 原著喺2006年2月9號歸檔. 喺November 20搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "8 held over suspected phishing fraud". The Daily Yomiuri. May 31, 2006.
{{cite news}}: CS1 maint: url-status (link)
- ↑ "Phishing gang arrested in USA and Eastern Europe after FBI investigation". 喺December 14搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Phishers Would Face 5 Years Under New Bill". Information Week. March 2, 2005. 原著喺2008年2月19號歸檔. 喺2007年8月13號搵到.
- ↑ "Fraud Act 2006". 喺December 14搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "Prison terms for phishing fraudsters". The Register. November 14, 2006.
- ↑ "Microsoft Partners with Australian Law Enforcement Agencies to Combat Cyber Crime". 喺August 24搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Espiner, Tom (March 20, 2006). "Microsoft launches legal assault on phishers". ZDNet. 原著喺2008年8月29號歸檔. 喺2007年8月13號搵到.
- ↑ Leyden, John (November 23, 2006). "MS reels in a few stray phish". The Register.
- ↑ "Overview of AOL anti-phishing activities". 喺March 08搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "AOL Takes Fight Against Identity Theft To Court, Files Lawsuits Against Three Major Phishing Gangs". 原著喺2007年1月31號歸檔. 喺March 08搵到.
{{cite web}}: Check date values in: |accessdate= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ "HB 2471 Computer Crimes Act; changes in provisions, penalty". 原著喺2021年3月22號歸檔. 喺March 08搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Brulliard, Karin (April 10, 2005). "Va. Lawmakers Aim to Hook Cyberscammers". Washington Post.
- ↑ "Earthlink evidence helps slam the door on phisher site spam ring". 喺December 14搵到.
{{cite web}}: Check date values in: |accessdate= (help); Unknown parameter |accessyear= ignored (|access-date= suggested) (help)
- ↑ Prince, Brian (January 18 2007). "Man Found Guilty of Targeting AOL Customers in Phishing Scam". PCMag.com. 原著喺2009年3月21號歸檔. 喺2007年8月13號搵到.
{{cite news}}: Check date values in: |date= (help); More than one of |archivedate=、|archive-date= specified (help); More than one of |archiveurl=、|archive-url= specified (help)
- ↑ Leyden, John (January 17 2007). "AOL phishing fraudster found guilty". The Register.
{{cite news}}: Check date values in: |date= (help)
- ↑ Leyden, John (June 13 2007). "AOL phisher nets six years' imprisonment". The Register.
{{cite news}}: Check date values in: |date= (help)
- ↑ Gaudin, Sharon (June 12 2007). "California Man Gets 6-Year Sentence For Phishing". InformationWeek. 原著喺2007年10月11號歸檔. 喺2007年8月13號搵到.
{{cite news}}: Check date values in: |date= (help)
拎
[編輯]- Anti-Phishing Working Group
- Bank Safe Online - Advice to UK consumers
- SecurityFocus - forensic examination of a phishing attack.
- Center for Identity Management and Information Protection – Utica College
- Plugging the "phishing" hole: legislation versus technology – Duke Law & Technology Review
- E-scams and Warnings Update - Federal Bureau of Investigation
- How the bad guys actually operate – Ha.ckers.org Application Security Lab
- Phishing Group at Indiana University
- Know Your Enemy: Phishing - Honeynet project case study
- The Phishing Guide: Understanding and Preventing Phishing Attacks – TechnicalInfo.net
- Phishing mailing list signup page